Before you begin evaluating software options, it’s crucial to understand your organization’s unique requirements. Start by assessing the size and structure of your organization. Are you managing a large enterprise with multiple locations or a small business with a single site? The scale of your operation will significantly influence your software needs.
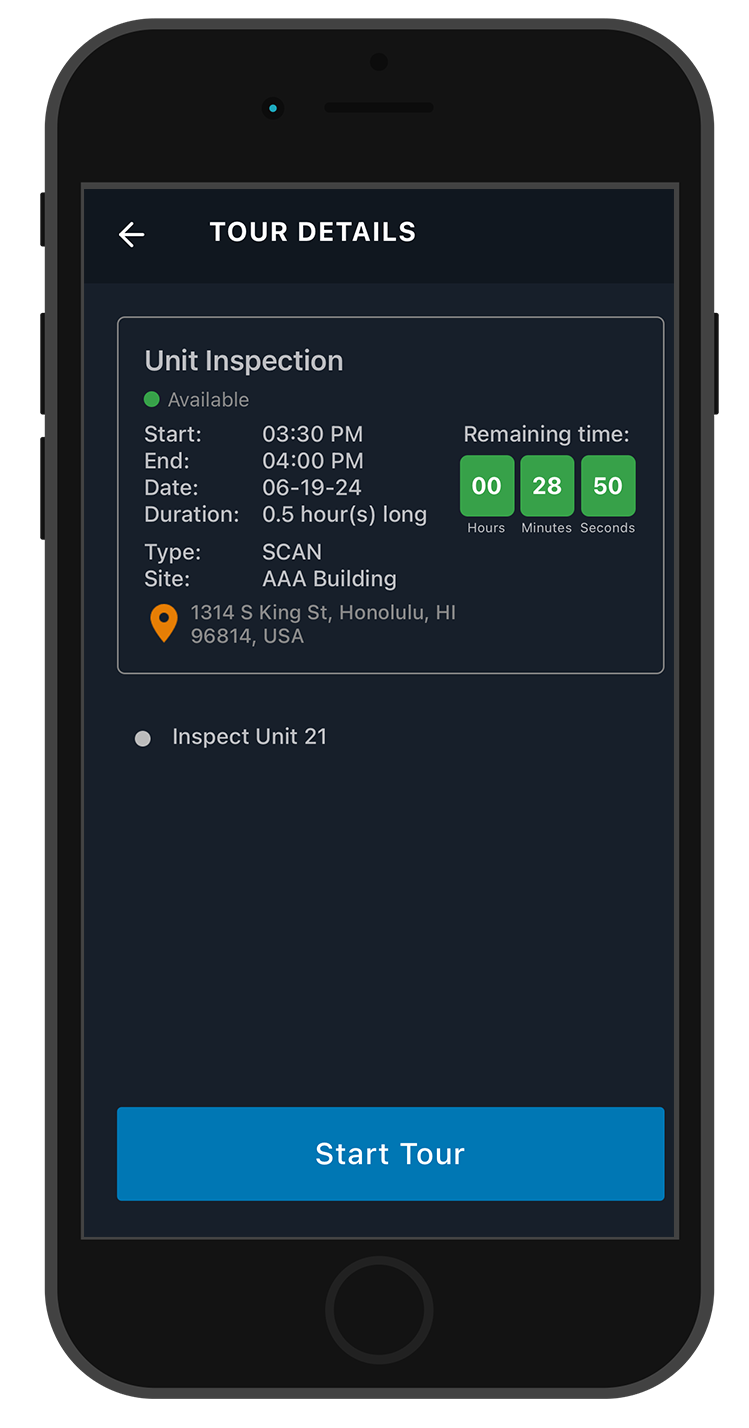
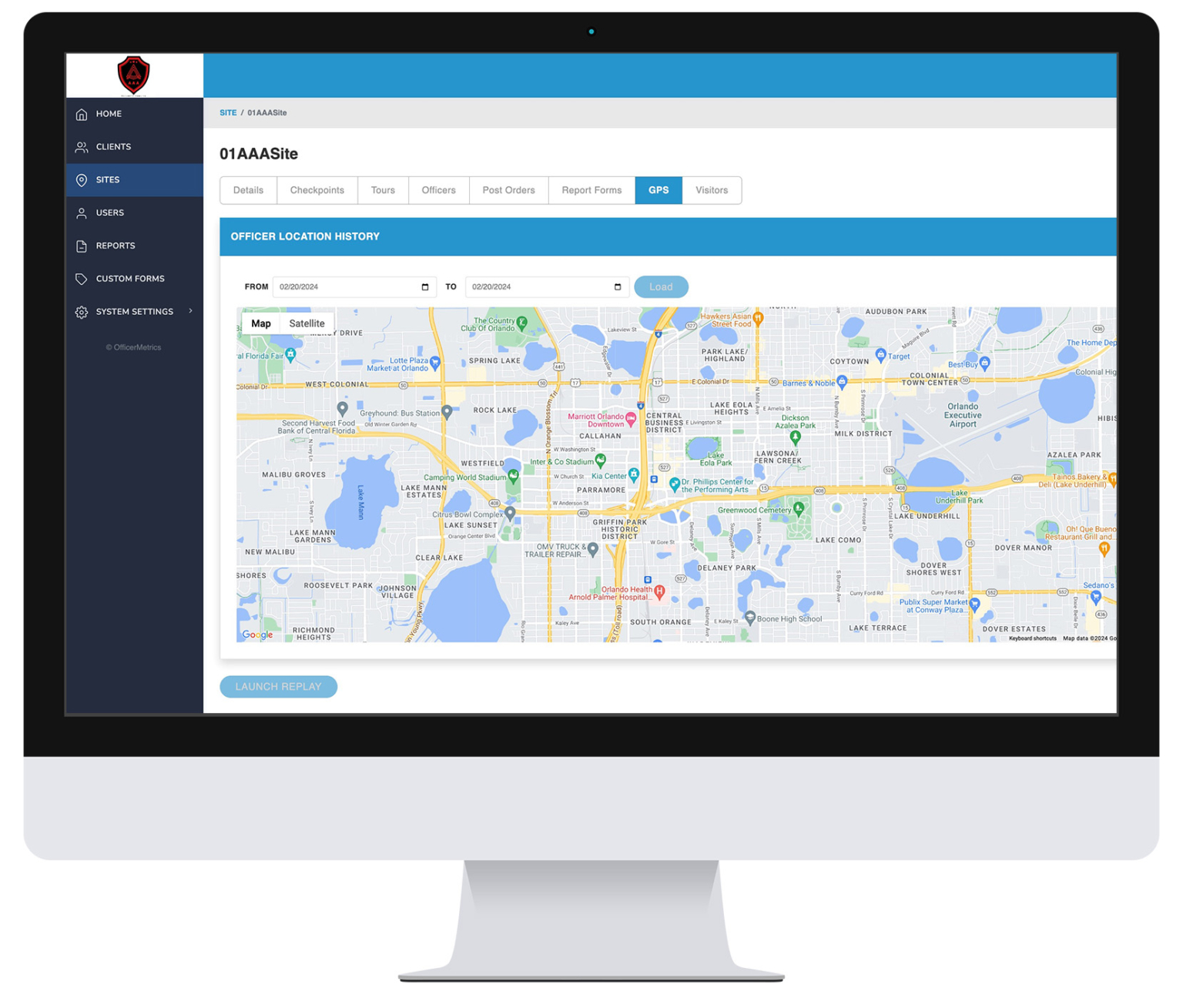
Next, consider your specific security requirements. Do you need comprehensive security incident reporting software, real-time location tracking, or seamless integration with existing systems? Identifying these requirements early will help narrow your focus to solutions that offer the features most relevant to your operations.
Additionally, it’s important to evaluate your current challenges and pain points. Are you struggling with manual reporting processes, lack of real-time data, or compliance issues? Understanding these challenges will guide you toward software that addresses your most pressing needs, making the selection process much easier.